What is security & Compliance?
Security & Compliance is about protecting systems and data and proving that protection meets required rules and standards.
What does AWS offer?
DDoS Protection on AWS
AWS offers multiple layers of protection against DDoS attacks:
AWS Shield
AWS Shield is a DDoS protection service with two tiers:
Shield Standard
This tier is enabled by default for all customers at no extra cost.
It offers protection against common L3/L4 attacks, (e.g. SYN/UDP floods).
Shield Advanced
This tier is an optional paid service that protects against more sophisticated and larger-scale attacks.
It includes 24/7 access to the DDoS Response Team (SRT) and cost protection during DDoS related usage spikes.
AWS WAF
AWS WAF, (Web Application Firewall) is used to protect web apps from common web exploits (Layer 7).
It can be deployed on:
- Application Load Balancer;
- API Gateway
- CloudFront
CloudFront & Route 53
These services can be used to enhance DDoS mitigation and availability.
How?
- Combine with AWS Shield for edge-based attack mitigation;
- Leverage global edge locations for high availability and performance.
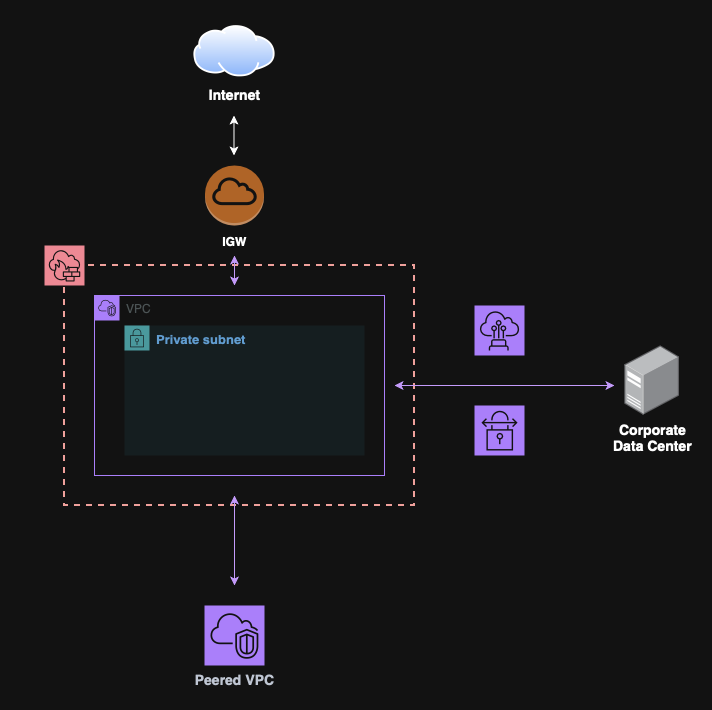
AWS Network Firewall
AWS Network Firewall is a managed firewall service for inspecting and filtering VPC traffic.
It protects for Layer 3 to Layer 7 attacks with deep packet inspection and stateless/stateful rules.
It integrates at the VPC level:
AWS Firewall Manager
AWS Firewall Manager provides a centralized management of firewall rules across an AWS organization.
It works wit AWS WAF, Shield Advanced and AWS Network Firewall to help maintaining consistent security policies.
AWS Certificate Manager (ACM)
AWS Certificate Manager (ACM) is a service to provision, manage and deploy SSL/TLS certificates.
AWS Certificate Manager (ACM) is free for public TLS certificates and provides automatic renewal and easy integration with AWS services.
AWS Secrets Manager
AWS Secrets Manager securely stores, rotates and manages secrets.
AWS Secrets Manager is integrated with RDS and supports automatic secret rotation.
Note: Secrets are encrypted using KMS.
Data Encryption
AWS Key Management Service (KMS)
KMS is a managed service to create, manage and control cryptographic keys used to encrypt data.
Key points:
- It is integrated with most AWS services, (e.g. S3, RDS, EBS, etc.);
- Supports AWS-managed keys;
- Offers automatic key rotation;
- Keys are protected using FIPS 140-2 validated hardware;
- Can perform envelope encryption, (encrypting data keys with master keys).
AWS CloudHSM
CloudHSM is a service that provides dedicated cryptographic key storage & operations.
Key points:
- Gives full control over HSMs and cryptographic keys;
- Compliant with FIPS 140-2 Level 3;
- Supports standard APIs like PKCS#11, Java JCE and Microsoft CNG;
Note: Compared to KMS, CloudHSM is much more complex & expensive, however, it provides more control & isolation.
Amazon GuardDuty
Amazon GuardDuty is an intelligent threat detection service using ML and anomaly detection.
GuardDuty uses inputs from CloudTrail, VPC flow logs and DNS logs to detect threats like cryptocurrency mining attacks.
Note: Optionally, it can use inputs from EKS, RDS, Aurora, EBS, Lambda and S3.
Amazon Inspector
Amazon Inspector is an automated vulnerability management service for workloads
It integrates with CI/CD and security tools while scanning EC2, ECR and Lambda for vulnerabilities.
Amazon Macie
Amazon Macie is a ML powered data security that discovers and protects sensitive data, (e.g. PII).
It is useful for compliance and regulatory needs, focusing on data classification and privacy.
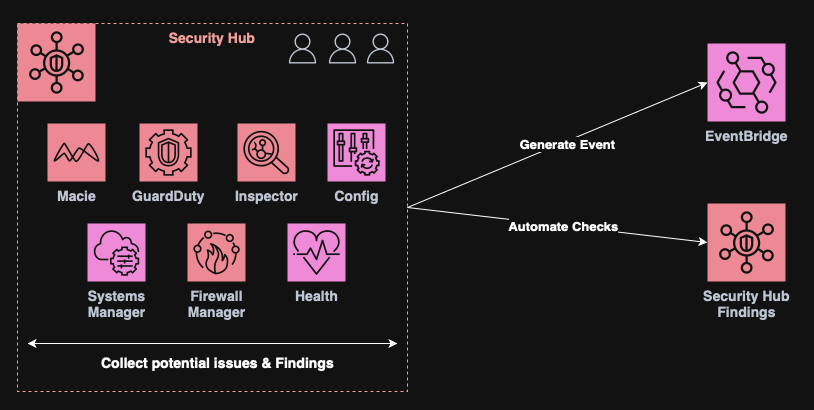
Security Hub
Security Hub is a centralized security posture management across AWS accounts.
It aggregates findings from services like GuardDuty, Inspector and Macie, providing a unified dashboard for compliance and threat visibility.
Amazon Detective
Amazon Detective is a security investigation tool to analyze and visualize AWS log data.
It helps understand the context behind security findings and works with GuardDuty, Macie and Security Hub.
IAM Access Analyzer
IAM Access Analyzer is part of IAM and analyzes policies to detect unintended access to resources.
Note: Requires defining a zone of trust.